







MobiLink Synchronization User's Guide
Transport-Layer Security
About transport-layer security
Public key cryptography makes use of mathematical systems that work with pairs of very large, associated numbers. These numbers, called keys, have particular properties. Each key can be used to encrypt information. Once encrypted, these messages can only be decrypted using the matching key.
One of the keys, called the public key, is published in a public forum. It can be used to encrypt information to be sent to the owner of the public key. The owner keeps the second key, called the private key, secret. A message encrypted with the public key can be decrypted only using the matching private key. Since the public key is published, anyone can create a message that only the owner of the private key can read.
In addition, a message encrypted with the private key can be decrypted by anyone who knows the public key. Such a message can be created only by someone who knows the private key. If the private key is kept secret, the owner can prove his or her identity by constructing such a message.
It is essential that the private key cannot be found easily through knowledge of the public key. The ease with which the private key can be derived from the public key is often associated with the strength of the cryptosystem and the size (in bits) of the public key. Another aspect of the private key is that it must be difficult to guess. The generation of high-quality private keys must incorporate pseudo-random data of high quality. If the data is predictable, it is easier for an adversary to guess the keys. To meet this criterion, the tools provided with MobiLink gather pseudo-random data from the operating system when generating new private and public key pairs.
Public-key cryptography has many advantages. Using the public key, anyone can send a message that can be read only by the person who knows the matching private key. Likewise, someone can prove that they know a private key by using it to encrypt a message. To verify the identity of a key owner, you can send an arbitrary message and ask them to encrypt. You can be sure that person knows the private key if you can decrypt the resulting message with their public key.
These features make public-key cryptography especially useful when establishing a secure communication link and happen automatically when you establish a synchronization connection using transport-layer security.
Once the secure link is established, the server and client automatically switch to a symmetric-key system of equivalent strength. In a symmetric system, the same key is used to encrypt and decrypt messages. This type of symmetric cipher can be computed more efficiently, reducing the computation time required to encrypt and decrypt messages.
Transport-layer security works by filtering all incoming and all out-going communication through the cipher of your choice. The translation occurs between the MobiLink synchronization server and the communication protocol of your choice. For example, adding security to a TCP/IP connection affects the architecture as shown in the following diagram:
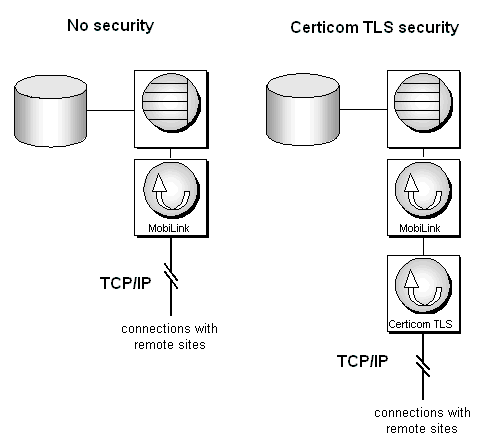
Transport-level security requires additional communication between a MobiLink client and the MobiLink synchronization server before the upload stream is sent. When a client initiates synchronization, it passes a message to the server. The client encrypts this message using the server's public key. The server decrypts this message using its private key. Initially, the server encrypts all messages to the client using the client's public key.
While this public-key/private-key cipher is secure as long as the private keys are kept secret, the encryption and decryption process is computationally intensive. To make further communication more efficient, the client and server agree upon and exchange another key and switch to a symmetric key cipher. They use this key and cipher for the rest of their communication because the symmetric cipher allows data to be encrypted and decrypted more efficiently.



