







MobiLink Synchronization User's Guide
Transport-Layer Security
When deploying a replication system, a large number of certificates may be required. The responsibility of signing many certificates may place too great a burden on the certificate authority. To lessen their workload, a certificate authority can delegate signing authority to others. To do so, the certificate authority signs a certificate held by the delegate. The delegate then proceeds to sign certificates using the private key that matches the one in this certificate.
A certificate chain is a sequence of certificates such that each certificate is signed by the next. The final certificate, called the root certificate, is owned by a certificate authority. For example, a server certificate can be signed by a delegate. The delegate's certificate can be signed by a certificate authority. The certificate authority's public key is contained in a third certificate. Such a situation is a chain of three certificates.
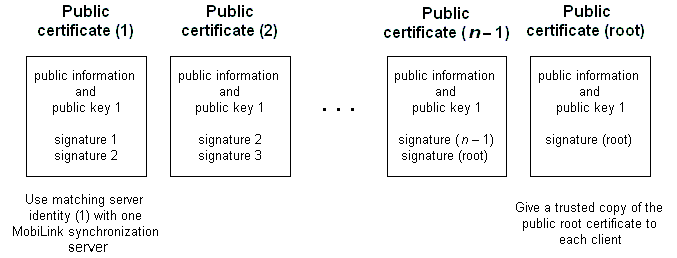
In fact, a delegate can also have delegates. Thus, a chain of certificates can be of any length. However, the final certificate is always a self-signed root certificate, owned by a certificate authority.
To trust a chain, a user must trust each of the following:
Before signing each certificate, the certificate authority and all delegates made certain that the identity information contained in the certificate correctly identified the certificate owner.
Each private key is known only to the certificate owner.
The user has a reliable copy of the certificate authority's public key.
All conditions are extremely important. The chain of certificates is only as strong as its weakest link.



